Workforce Development

Work With Us
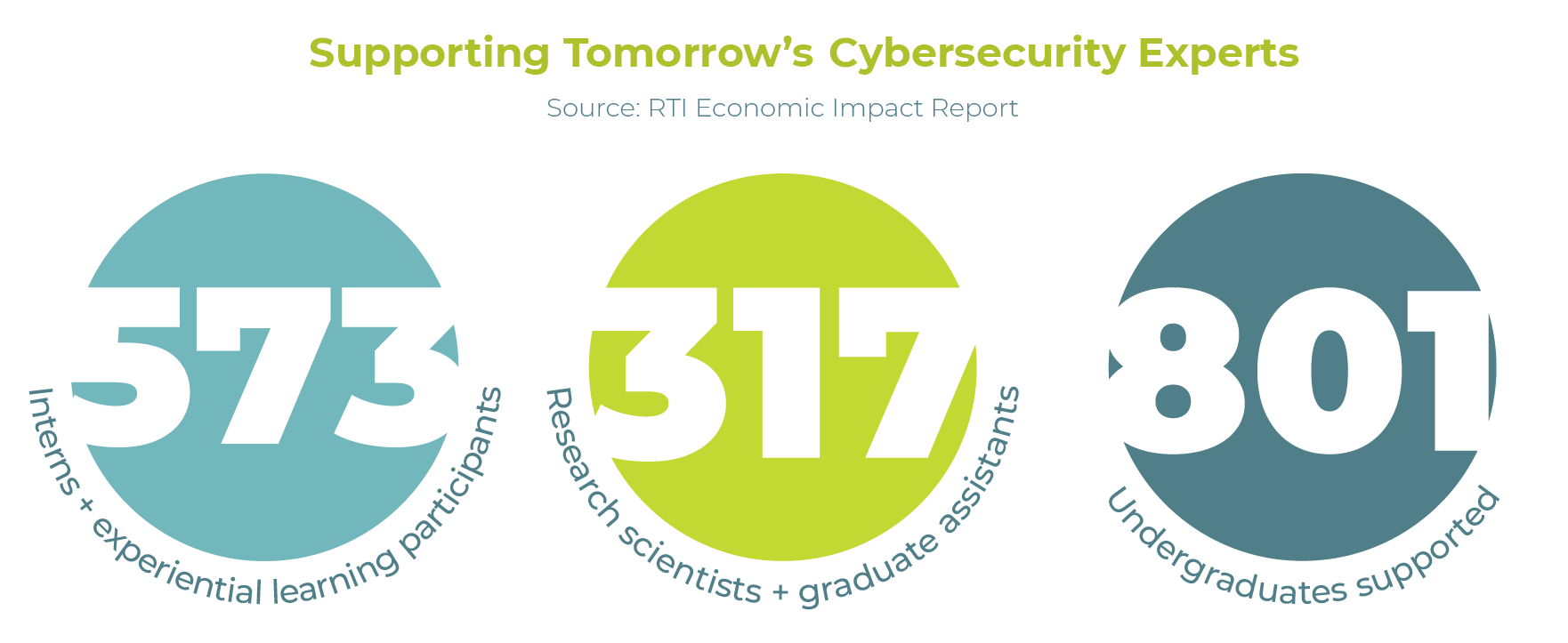
CCI is connecting companies with talented, motivated students, who are screened for the skills your organization needs. An unprecedented coalition of more than 40 Virginia universities and colleges, CCI has incredible reach across the state.
We've built programs that give students the experience they need to have successful careers in cybersecurity. Our programs make it easy for you to connect with future employees and interns. The CCI program roster includes Project-Based Learning, Clearance Preparedness, our signature Internship and Job Fair, and the Cyber Fusion capture-the-flag competition and job fair. Let's get to work!
Project-Based Learning
The CCI Project-Based Learning Program is a win-win for companies and students alike. Companies get to know students and directly learn what they can do. Students gain mentoring and work on projects important to industry needs. CCI funds this program and the student stipend.
We work with you to create a project tailored to your needs, screen the applicants based on your criteria, and deliver a talented pool of applicants for your final selection.
GuidePoint Security is seeking apprentices to help create a “SOC-in-a-Box,” which is a scalable and quickly deployable lab environment. The environment should include all essential elements of a Security Operations Center (SOC), including a log aggregation platform, case management system, basic active directory ecosystem, and a host-based detection tool.
Students will have the opportunity to actively contribute to strengthening PBS's data privacy program. Students will gain hands-on experience by developing cross-functional privacy intake requests, conducting data discovery and classification assessments, and supporting the design of governance frameworks. Through these efforts, students will play a key role in enhancing organizational data protection and advancing cybersecurity resilience.
This project provides students the opportunity to work on a secure IoT protocol designed to help leverage the benefits of the IoT devices without creating excess risk to the security of critical government networks and systems.
Get Clearance Ready!
We're prepping students about the benefits of holding a security clearance and the approval process. We draw upon experts from government and industry to discuss the fulfilling work that holding a security clearance can bring as well as the pitfalls to avoid. This program provides a great introduction for you to discuss your mission directly with students while helping them on their career path.
The 2026 sessions begin in February. Registration is open for this free informational seminar series. By attending the six bi-monthly 60-minute virtual modules, you'll learn about the clearance process and what you can expect in clearance-level roles.
Sessions will also allow participants to connect and interact with industry professionals. You'll be awarded a digital badge when you complete the program.
If you weren't able to attend the Clearance Preparedness sessions in person, get caught up by watching the recordings.
Cyber Fusion
Virginia Military Institute and CCI co-host this annual invitation-only capture-the-flag style competition and job fair. In addition to competing in various challenges, this event connects high-achieving students with companies and government agencies, providing speaking opportunities and a job fair to showcase organizations and engage with top cybersecurity talent.
Cyber Fusion is open to Virginia colleges and universities that are designated National Centers of Academic Excellence in Cyber Defense.
For more information, please contact Sarah Hayes at sshayes@vt.edu. We look forward to working with you!
-
General Item
-
General Item
-
General Item
-
General Item
-
General Item
-
General Item