Virginia Cybersecurity Challenge
The Commonwealth Cyber Initiative (CCI), in partnership with US Ignite, is hosting the Virginia Cybersecurity Challenge to accelerate Virginia’s development of talent and products that enhance cybersecurity.

The Challenge sought submissions from researchers and faculty members at public CCI member universities to develop a cybersecurity prototype that leverages unique elements of emerging 5G technologies to provide secure operations or communications in ways not possible on previous generation networks.
This prototype will ultimately develop into a commercializable product solution. Undergraduate and graduate students were encouraged to participate actively on researcher-led teams.
Partnership advances innovation
Virginia has emerged as a national leader in cybersecurity, boasting the second-highest concentration of technology workers in the nation.
The Commonwealth considers it vital that Virginia researchers and students take advantage of opportunities to explore cybersecurity via programs such as this Challenge.
CCI aims to create a commonwealth-wide ecosystem of innovation excellence at the intersection of cybersecurity, autonomous systems, and data. Our mission includes research, innovation, and workforce development.
Secure 5G networks will become the backbone to enable IoT, transportation, automated infrastructure, and other autonomous systems of the future. The security of these networks and devices will touch nearly every aspect of people’s lives and help drive digital transformation and jobs.
This gated, four-phase Challenge began May 5, 2021. This call invited researchers to submit a Phase I proposal, with finalists from each phase awarded funds and an invitation to participate in the next phase.
2021 Winning Projects
The Internet of Things (IoT) presents great opportunity for device connections. The growth of 5G technology will result in faster internet resource access and extension of connection boundaries. 5G technology combined with other factors means an increased interest in device connection to the IoT. Legacy devices are older, still fully operational, and not equipped to connect to the IoT. Sensitive devices have been excluded from IoT consideration because of devastating potential attack vectors. Many devices pre-date IoT hardware.
This project offers a connection solution for those devices. The passive IoT connection device collects data about the legacy device and packages it for IoT consumption. The data collected is operational, positional, and functional and is then encrypted as an object for the device owner to manage in an IoT style. The device can be paired with a sensitive device, becoming its IoT connection. The sensitive device would still have an air gap and not be directly connected to the IoT.
The project is a community college implementation and education project. Details of the prototype are available, along with a study identifying key characteristics of a sustainable, lab-based student research course.
This project proposes web-based modeling and analytical environment prototype for predicting the spread of malicious behaviors and computer viruses (as contagions) on 5G networks. We recast real 5G networks in an abstract simulated graph form. The goal is to run offline and real-time intensive data analytics and simulations to see the effects of viruses, network topological structures, devices, and applications behavior, and propose intervention strategies by blocking nodes or altering network structure to avoid cascading failures. This work will be beneficial to cybersecurity analysts, researchers, businesses IT professionals, and students.
This work will use a novice approach to view the 5G network as a complex system of components that interact together. The spread of viruses, malware, or other infections will be predicted according to prescribed behavior models assigned to each device. The environment will employ multiple scenarios to provide a threat evaluation and execute blocking strategies automatically. In addition, the environment will have a dedicated dashboard for security analysts to manually input various modeling parameters and evaluate the outcomes, promoting the concept of “analyst in the loop.” The proposed system will have additional features provided through the dashboard to query and visualize networks, subnetworks, and their properties.
Modern buildings strive to enhance resilience and meet environmental goals. As various systems such as heating/cooling are automated and are communicating wirelessly with devices in these buildings, appropriate mechanisms using 5G must be devised to make the systems and their communications hacker-proof. At the same time, the systems and devices in the building must be controlled centrally and must be provided with the ability to “learn” heating/cooling patterns from power usage, location, etc., to operate effectively over time. This proposal aims to harness existing technology at the Virginia Commonwealth Cyber Initiative Northern Virginia node on 5G security to devise one mechanism to securely communicate over 5G between systems and devices. The second aim of the proposal is to develop server software with learning capabilities for heating/cooling and with the ability to communicate the recommended changes in heating/cooling securely to devices across the building. The commercialization plan includes focus groups with property developers and builders who will be the main customers for the product. The services of the Center for Innovation and Entrepreneurship at School of Business, the Law Clinic at the Scalia Law School, and the Small Business Development Center at George Mason University will be utilized for successful commercialization.
As the paradigm of the Internet of Things evolves into an essential component of modern life, securing its underlying cyber-physical systems grows increasingly crucial. Electromagnetic sabotage or Intentional Electromagnetic Interference involves intentional malicious use of electromagnetic sources to disrupt electronic equipment performance (e.g., injecting electromagnetic pulses directly into electronic systems, jamming electromagnetic wave-based communication etc.). The damage thus inflicted can range from subtle disturbances that cause data stream errors to massive disruptions that cause permanent system damage. Electromagnetic interference shielding materials that traditionally form the first line of defense to mitigate this cyber threat tend to convert electromagnetic radiation into heat dissipation, and in extreme cases, prolonged exposure to electromagnetic radiation results in thermal instability that adversely affects device performance.
To address this issue, this project is centered on developing a novel composite material comprising of a phase change material modified by the inclusion of tailored magnetic particles with high microwave absorption efficiency, thereby creating a compact, conformal multifunctional coating that can simultaneously provide high-frequency electromagnetic radiation shielding and passive thermal management for microwave devices operating in the X-band (8-12 GHz). At this initial stage, a proof-of-concept demonstration of this innovation will focus on applying the coating to the substrate of a planar self-biased ferrite circulator – a crucial three-port component in an RF front-end module.
Enabling pervasive inter-connectivity between heterogeneous IoT environments is now possible given the capabilities of the current 5G paradigm. In such a 5G-enabled ubiquitous environment, enabling dynamic interoperability and seamless scalable cooperation between IoT devices requires a uniform representation of device identity and scalable authentication and identification mechanisms. Enabling privacy-friendly, computationally efficient, reliable D2D authentication is still a crucial problem for such limited resources devices. As a motivation to alleviate such problems, we introduce in this proposal a novel decentralized trustworthy SSI identity management solution denoted as Proactive Trustworthy Self-Sovereign Identity Management (PT-SSIM). PT-SSIM design follows the core infrastructure of Self Sovereign Identity (SSI) model while introducing extra layers of identity protections and identification services free of any information disclosures. PT-SSIM embraces the proactive Moving-target Defense concept in obfuscating the identity credentials to be externally stored in a distributed manner. PT-SSIM integrates the Proactive Shamir’s Secret Share scheme with the Blockchain-based smart contract technology to provide transparent and trustworthy SSI-based DIMs for 5G IoT systems.
Transportation Cyber-Physical Systems (TCPS) is envisioned as a distributed system composed of devices in vehicles, roadside units, traffic lights, sensors, and etc., and personal devices. 5G networks will help realize such a connected world and become the backbone to enable TCPS. The biggest threat facing autonomous vehicles in TCPS is cybersecurity. Specifically, vehicle-to-infrastructure (V2I) communication presents a variety of vulnerabilities that create an attractive target for attacks such as the false information insertion attacks which may cause threats to driving safety and human life. However, previously proposed methods of false information detection may not meet the real-time requirement for safety-critical applications in V2I communication in TCPS. Emerging approaches use machine learning techniques for real-time detection. In this project, we will develop, implement and deploy software prototypes for the prior research results for the false information attack creation and detection from our team and the community in the V2I communication in TCPS.
Resources
Questions? Please contact us at challenges@us-ignite.org with any questions.
Please submit proposals by Oct. 15, 2021 to proposals@cyberinitiative.org.

If you'd like to schedule a 20 min call to learn more about the Virginia Cybersecurity Challenge, please complete this form and we will follow up shortly.
Missed the information session on May 21? Watch it now on YouTube!
Phases
Participants will:
- Submit an initial proposal in the format described below, responding to the Challenge pitch and outlining the proposed project, the potential for commercial success, success metrics, target audience, budget and identified commitment for the prototyping phase of the Challenge, as well as team biographies.
- This proposal will respond to the following pitch:
A cybersecurity prototype and relevant resources that leverage unique elements of emerging 5G technologies to provide secure operations or communications in ways not possible on previous generation networks.
Over the course of 6 months, invited participants will:
- Develop a proof-of-concept prototype based on the proposal submitted during Phase I.
- Demonstrate a functioning prototype for evaluation by a panel of expert judges.
- Submit a brief proposal for product development in phase III, including a budget and identified commitment.
Over the course of 6 months, invited participants will:
- Develop operational and scalable products based on the prototypes submitted during Phase II.
- Demonstrate a functional application before a panel of judges for evaluation.
- Submit a brief proposal for commercialization or adoption of the technology or application by industry
Over the course of 3 months, invited participants will fully engage with commercialization activities led by US Ignite and partners.

Eligibility
Researchers and faculty members at public institutions of higher education in CCI who are deemed eligible by their home institution to serve as a Principal Investigator (PI) on an external grant are eligible to apply.
Applications from under-represented groups are particularly welcome, as are applications from researchers who have not previously engaged with CCI.
Students at eligible CCI institutions are encouraged to reach out to researchers who are eligible to serve as a PI to participate on a project. Similarly, Virginia-based researchers are encouraged to recruit interested students to join researcher-led teams and continue on to the commercialization phase.
Awards
Following Phase I, Challenge judges will invite up to seven (7) teams to move on to Phase II, awarding each finalist up to $20,000.
Following Phase II, Challenge judges will invite three to five (3-5) teams to move on to Phase III, awarding each finalist up to $32,000.
Following Phase III, Challenge judges will invite two (2) teams to move on to Phase IV, which will support teams in developing commercialization strategies. and efforts.
Please note: this Challenge is a gated competition. Only teams selected at the end of each phase will be invited to participate in the next phase.
Successful applicants are expected to participate fully in the activities of CCI, including providing materials needed for reports, participation in CCI meetings, and responding to data collection requests by CCI. All publications and presentations resulting from the grant should acknowledge support from the Commonwealth Cyber Initiative (CCI). Grant award letters will supply an example of this acknowledgement.
Restrictions. According to the terms under which CCI is funded, the following costs are not allowable:
- Indirect costs.
- Costs of developing and delivering undergraduate capstone programs, except as part of the larger effort to align cyber and CPSS-focused undergraduate program content with industry needs.
- A portion of salaries and benefits of faculty for time spent teaching undergraduates, including teaching cyber-related courses.
- Scholarships for costs of attendance at institutions of higher education.
Identified Commitment
Because this is a CCI Node-funded program, the awardee must provide a 1:1 identified commitment to this grant. While indirect costs (IDC) are NOT eligible costs in the proposals submitted in response to this RFP, unrecovered IDC can be used to partially fulfill this requirement. No funds from other CCI-funded projects can be used as identified commitment.
Proposals and budgets should go through the appropriate approval process at the PI’s institution. For instance, many universities require researchers to include a proposal and budget which have been approved in the standard OSP pre-award procedure.
Proposal Format
Please submit proposals by Oct. 15 to proposals@cyberinitiative.org.
Proposals must use 1-inch margins, 11-point font or larger (Arial or Helvetica), and single line spacing. The following outline is to be followed for Phase I:
- Title page (up to 1 page), including:
- Title of the proposed project
- PI Name
- PI affiliation
- PI contact information
- Proposed project (up to 2 pages), including:
- A clear statement of the proposed cybersecurity prototype and approach.
- Discussion of the technical requirements and engineering/scientific justification.
- Description of the potential for the prototype (and ultimately product) to deliver substantive innovation within 5G cybersecurity.
- Discussion of market potential likely to open up avenues for research and/or workforce development.
- Proposed commercialization or industry adoption strategy (up to 1 page).
- Budget and budget justification (up to 1 page).
- The budget must contain both the requested amount and the identified commitment. The latter should be in the form of a table according to the following format:
- Download worksheet PDF.
- Biography (up to 2 pages). Use NSF format.
| Event | Date |
|---|---|
| Call for Proposals Released | May 5, 2021 |
| Question Period Ends | May 14, 2021 |
| Proposers Workshop | May 21, 2021 |
| Phase I Proposal Submissions Due | Oct. 15, 2021 |
| Phase I Award Notification/Phase II Start | Oct. 29, 2021 |
| First round of award funding disbursed. | |
| Phase II Prototype Submissions Due | Feb. 25, 2022 |
| Phase II Award Notification/Phase III Start | March 11, 2022 |
| Second round of award funding disbursed | |
| Phase III Product Submissions Due | Aug. 15, 2022 |
| Phase III Recognition and Public Review | Aug. 29, 2022 |
| Phase IV Commercialization Activities Commence | Sept. 12, 2022 |
- Phase I: May 5, 2021 ー Oct. 15, 2021
- Phase II: Oct. 29, 2021 ー Feb. 25, 2022
- Phase III: March 11, 2022 ー Aug. 15, 2022
- Phase IV: Sept. 12, 2022 ー Dec. 16, 2022
The Phase I proposal must be submitted via email to proposals@cyberinitiative.org no later than the close of business (5:00 p.m. ET) on Friday, Sept. 3, 2021.
Please indicate “CCI Cybersecurity Challenge_PI Last Name” in the subject line.
All proposals must be submitted as a single PDF document.
A committee including representatives from CCI, outside technical experts, and US Ignite will review the proposals and make award recommendations. Evaluation criteria will include demonstrated expertise in at least one of the following areas:
- Understanding of cybersecurity requirements within 5G technologies; network architecture; and identity management.
- Potential for the prototype (and ultimately product) to deliver substantive innovation within 5G cybersecurity.
- Feasible commercialization strategy and market potential (offering potential for job creation within the Commonwealth)
- Clear performance and evaluation metrics proposed for the project.
- Sufficient budget and matching resources to develop prototype
- Track record of the PI/team involved and likelihood of achieving the stated goals.
I’m a recent graduate of a college or university in the Commonwealth of Virginia. Can I serve as a PI?
Only faculty or researchers are eligible to apply for grant funding as a PI at a public CCI member institution may apply to this Challenge. Students are encouraged to reach out to a PI to participate on a project.
Do I need a team to apply?
The PI may lead a team of any size for this competition. The PI will serve as a team lead and all competition correspondence. All awarded funds will be disbursed to the PI.
Is there a registration fee?
There is no registration fee to apply.
What is required for each submission?
Each phase requires different materials for submission, but all submissions must include a budget and justification. Budget information should only be 1-2 pages of material.
Informational Workshop FAQ
I am a principal investigator (PI). If I have a student on my team, will they need to do anything (e.g., paperwork) prior to submission?
We strongly recommend you run your proposal through your OSP structure to review the budget and ensure your proposal follows the regulations of your institution. Your proposal must be reviewed by the sponsored program personnel within your institution. If you have already selected a student, feel free to mention any special qualifications they have, their proposed responsibilities, and duration of performance (if applicable).
I’m a PI and would like a student to join my Challenge team. Do I need to identify this student at the point of submission?
You will need to identify the student position in your budget, but will not need to identify a particular student at the point of submission. Also, please review the response to question 1 above.
I’m a student looking to join a Challenge team. Is there a list of PIs participating in this Challenge that I can refer to?
CCI does not currently have a list of the PIs participating in this competition. However, CCI can provide a list of PIs that have previously engaged with CCI in other ways, please visit CCI’s people’s page.
Any faculty member or researcher eligible to be designated as a PI by any of CCI’s 40 participating institutions is eligible to submit a proposal. If a faculty member or researcher hasn’t engaged with CCI before, they are more than welcome to submit. We suggest searching for faculty members or researchers within your institution’s expert in cybersecurity, computer science, wireless communications, architecture, etc. Students cannot submit a proposal by themselves. A proposal must come through one of the researchers whom your educational institution identifies as being an eligible PI.
There are many avenues you can take to find a PI, so think broadly. CCI has funded other opportunities that had PI’s from departments such as geography, cyber biosecurity, agriculture, political science, education, communications, and more. Keep your mind open within the scope of the call in all possible areas where innovation can occur. The call’s focus is cybersecurity, autonomous systems, and intelligence, which is a technical focus, but it often involves expertise outside of the core security area.
Can the project idea be related to 6G networks?
Yes, we are looking for advanced wireless solutions broadly interpreted.
Is there a set number of persons on a team, or a max number?
There is no minimum or maximum number of persons on a team. The number of team members is up to you, but we advise you to be cognizant of the budget available and what the team hopes to achieve.
Additional Resources
● ICAP: Josh Green is the Director of the Innovation Commercialization Assistance Program (ICAP), Virginia Small Business Development Center Network with George Mason University. Josh will assist with the commercialization phase of the Challenge. Find more information on ICAP below, along with Josh’s contact information.
● VA Cybersecurity Challenge Informational Workshop Presentation
● US Ignite 5G Background Information
If you have any additional questions following this workshop please reach out to challenges@us-ignite.org
Success Stories
Here are some of the prize-winning ideas submitted to past US Ignite Challenges and Competitions.
Road Vision – George Washington University
Tasked with creating an app to help address fundamental city challenges, the GWU team developed Road Vision, which uses Artificial Intelligence (AI) technology to analyze video feeds and translate visual data into useful traffic and public safety information. As the competition winners, the team earned $25,000 in start-up and research funding. The team used the funding to pursue growth and application scale.

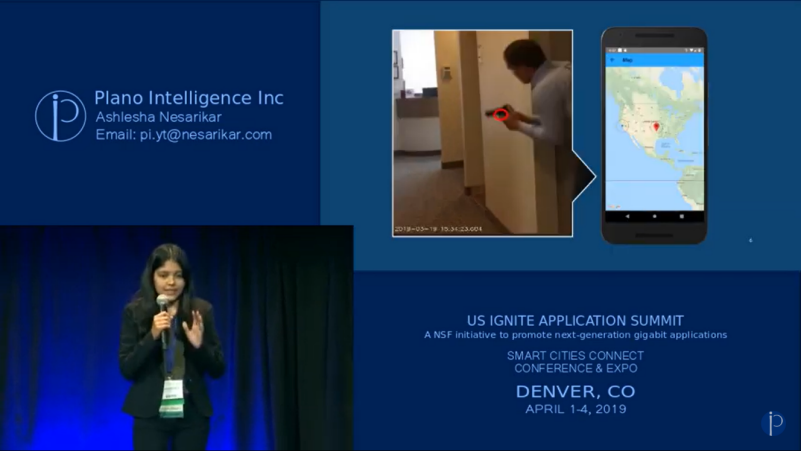
Plano Intelligence Inc. – SCHOOL
The winner of a reverse pitch challenge competition held in Richardson, TX, Ashlesha Nesarikar, pitched an AI platform called iNotify that recognizes wielded guns in prohibited areas to reduce gun violence.
Plano Intelligence continues to be a thriving startup committed to the constructive social impact of AI featuring a privacy and security centric cognitive AI platform, iCognet, that is a reusable, plug & play, and versatile foundation for existing and future AI applications.
“We are talking with people, with actually all around the Nation…US Ignite has helped us get to this point. We ended up winning the prize from them and the ability to use the UNICEF infrastructure” – Ashlesha Nasarikar, Founder and CEO Plano Intelligence
Specific questions concerning this call and the requirements set forth herein should be directed in writing to the email address: proposals@cyberinitiative.org.


